Cyber espionage is an ever-increasing threat in today’s interconnected world. It involves the unauthorized access, theft, or manipulation of sensitive information for political, economic, or military gain. With the rise of sophisticated cyber attacks, the role of cyber security in protecting against cyber espionage has become paramount.
In recent years, cyber espionage has targeted governments, businesses, and individuals, with devastating consequences. One striking example is the 2014 cyber attack on Sony Pictures Entertainment, where a group believed to be linked to North Korea infiltrated the company’s network and stole confidential data, resulting in reputation damage and financial losses. To combat such threats, effective cyber security measures are crucial.


Understanding Cyber Espionage and Its Threats
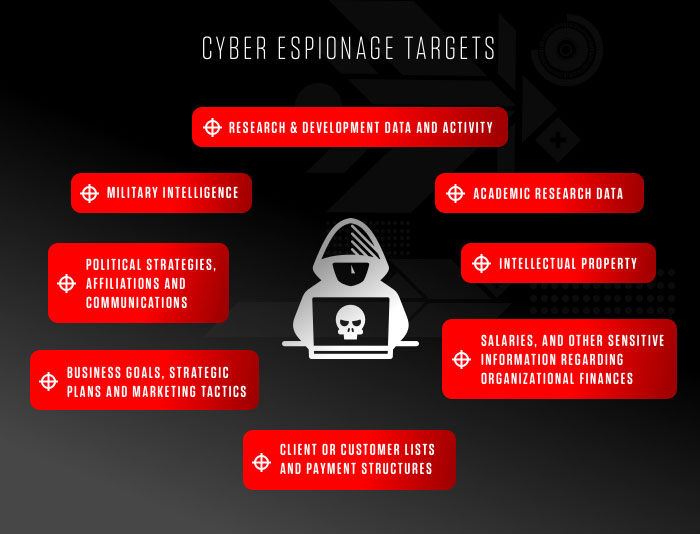
Cyber espionage refers to the act of infiltrating and gathering sensitive information from computer systems, networks, and databases of individuals, organizations, or governments. It involves unauthorized access to confidential data with the intention of gaining a competitive advantage, political advantage, or financial benefit. The digital age has given rise to sophisticated cybercriminals and state-sponsored hackers who use advanced techniques to breach security systems and exploit vulnerabilities.
In today’s interconnected world, cyber espionage poses a significant threat to national security, economic stability, and individual privacy. The stolen information can be used for a variety of malicious purposes, including industrial espionage, intellectual property theft, political manipulation, and surveillance. The potential damage caused by cyber espionage is extensive and can have far-reaching consequences.
Cybersecurity plays a crucial role in protecting against cyber espionage. By implementing robust security measures and adopting proactive strategies, individuals and organizations can minimize the risk of falling victim to these cyber threats.
The Importance of Cybersecurity in Preventing Cyber Espionage
Effective cybersecurity practices are essential in preventing and mitigating the risks associated with cyber espionage. Here are some key reasons why cybersecurity is crucial:
- Protection of Sensitive Information: Cybersecurity measures safeguard sensitive information from unauthorized access, ensuring the confidentiality and integrity of data. By employing encryption techniques, firewalls, and user authentication protocols, organizations can protect their valuable information from falling into the wrong hands.
- Prevention of Data Breaches: Cybersecurity measures help detect and prevent data breaches that can lead to unauthorized access and theft of confidential information. Robust security systems, regular vulnerability assessments, and employee training on cybersecurity awareness can significantly reduce the risk of data breaches.
- Mitigation of Financial Losses: Cybersecurity helps in minimizing financial losses associated with cyber espionage. The cost of recovering from a cyber attack can be substantial, including expenses related to incident response, legal costs, reputation damage, and potential fines for non-compliance with data protection regulations.
Cybersecurity Strategies for Protecting Against Cyber Espionage
To effectively protect against cyber espionage, organizations must implement robust cybersecurity strategies that address potential vulnerabilities. Here are some key strategies:
- Implement Strong Access Controls: Ensure that access to sensitive information is limited and granted only to authorized individuals. Implement multi-factor authentication and regularly review user access privileges to prevent unauthorized access.
- Regularly Update and Patch Systems: Keep all software, operating systems, and applications up to date with the latest security patches to address known vulnerabilities. Regularly monitor for updates and apply them promptly.
- Train Employees on Cybersecurity Awareness: Educate employees about cybersecurity best practices, such as identifying phishing emails, using strong passwords, and avoiding suspicious websites. Regular training sessions and awareness campaigns can help create a security-conscious workforce.
- Use Encryption and Secure Communication: Encrypt sensitive data both at rest and in transit. Implement secure communication protocols, such as virtual private networks (VPNs), to protect data transmission between different networks.
The Role of Cyber Threat Intelligence in Preventing Cyber Espionage
Cyber threat intelligence provides valuable insights into potential threats and helps organizations enhance their cybersecurity posture. It involves the collection, analysis, and dissemination of information about emerging cyber threats, including techniques used by cybercriminals involved in cyber espionage.
By leveraging cyber threat intelligence, organizations can anticipate and proactively respond to cyber threats, including those related to cyber espionage. Here are some key benefits of utilizing cyber threat intelligence:
- Early Warning System: Cyber threat intelligence provides early indicators of potential attacks, allowing organizations to take preventive measures before an attack occurs. This enables proactive defense and reduces the likelihood of successful cyber espionage attempts.
- Improved Incident Response: By understanding the tactics, techniques, and procedures (TTPs) employed by threat actors involved in cyber espionage, organizations can develop more effective incident response plans. This helps in minimizing the impact of an attack and accelerating the recovery process.
- Enhanced Risk Assessment: Cyber threat intelligence provides valuable information for risk assessment and helps organizations identify vulnerabilities, potential targets, and attack vectors commonly used in cyber espionage. This enables organizations to prioritize security measures and allocate resources effectively.
Sources of Cyber Threat Intelligence
To effectively utilize cyber threat intelligence, organizations can rely on various sources for gathering information. Some common sources include:
- Cybersecurity Vendors: Many cybersecurity vendors offer threat intelligence services and provide valuable insights into emerging cyber threats and attack trends.
- Government Agencies: Government agencies, such as national security and intelligence agencies, often share threat intelligence to help organizations protect against cyber threats.
- Information Sharing and Analysis Centers (ISACs): ISACs facilitate information sharing among member organizations within specific industry sectors. They provide a platform for sharing threat intelligence and collaborating on cybersecurity initiatives.
- Open-Source Intelligence: Open-source intelligence refers to publicly available information from forums, social media, and other online sources. Such information can provide insights into emerging cyber threats.
The Role of Incident Response in Cyber Espionage Defense
In the face of cyber espionage attacks, an efficient and well-prepared incident response plan is essential to mitigate the impact and recover quickly. Incident response refers to the process of identifying, responding to, investigating, and recovering from cybersecurity incidents.
Here are some key components of an effective incident response plan:
- Preparation: Develop an incident response plan that outlines roles, responsibilities, and procedures for detecting, analyzing, and responding to cybersecurity incidents. Regularly test and update the plan to address emerging threats.
- Detection and Analysis: Implement monitoring tools and techniques to detect potential security incidents. Establish procedures to assess the severity and impact of incidents and gather relevant information for analysis.
- Containment and Eradication: Isolate affected systems and networks to prevent further damage. Apply necessary security patches, remove malicious software, and remediate vulnerabilities to eradicate the threat.
- Investigation and Recovery: Conduct a thorough investigation to determine the root cause of the incident. Gather evidence, document findings, and take appropriate actions to recover from the incident, restore systems, and enhance security.
- Post-Incident Activity: Evaluate the effectiveness of the incident response process and identify areas for improvement. Update security controls, policies, and procedures based on lessons learned.
Collaboration and Information Sharing in Incident Response
Incident response often involves collaboration and information sharing among various stakeholders, including internal teams, external partners, and relevant authorities. Timely and accurate sharing of information is crucial for effective incident response. Organizations can benefit from:
- Establishing Communication Channels: Implement secure and reliable communication channels for incident response coordination. This can include dedicated communication platforms, encrypted messaging applications, and incident reporting mechanisms.
- Engaging External Partners: Engage with external partners, such as incident response teams, cybersecurity vendors, and legal counsel, to seek additional expertise and support during incident response.
- Participating in Information Sharing Programs: Join industry-specific information sharing programs or initiatives that facilitate the exchange of threat intelligence and best practices among participating organizations.
Conclusion and Additional Resources
In conclusion, cyber espionage poses a significant threat in today’s digital landscape, and effective cybersecurity measures play a crucial role in protecting against these threats. By implementing strong access controls, regularly updating systems, and training employees on cybersecurity best practices, organizations can enhance their defenses against cyber espionage.
Furthermore, leveraging cyber threat intelligence and having a well-prepared incident response plan are essential for detecting, mitigating, and recovering from cyber espionage attacks. Collaboration and information sharing among stakeholders are also crucial in effective incident response.
To stay up to date with the latest trends and insights on cyber security and cyber espionage, you can visit reputable cybersecurity websites, follow industry blogs and news sources, and participate in relevant conferences and events. By staying informed and proactive, individuals and organizations can better protect themselves against the ever-evolving landscape of cyber threats.
The Role of Cyber Security in Protecting Against Cyber Espionage
- Cyber security plays a crucial role in safeguarding against cyber espionage.
- It helps in detecting and preventing unauthorized access to sensitive information.
- By implementing strong security measures, organizations can minimize the risk of cyber espionage attacks.
- Regularly updating and patching software and systems is essential in protecting against cyber espionage.
- Training employees about cyber security best practices can help in preventing cyber espionage incidents.
Cyber security plays a crucial role in protecting against cyber espionage.
By implementing strong security measures and staying updated on the latest threats, organizations can safeguard their sensitive data and prevent unauthorized access.
Through the use of firewalls, encryption, and secure protocols, cyber security professionals work to detect and mitigate potential cyber attacks.
Furthermore, fostering a culture of security awareness and providing training can empower employees to identify and report suspicious activities.
Overall, cyber security is a vital defense in the fight against cyber espionage, ensuring the protection of critical information and maintaining the integrity of organizations.
Remember, being cautious online and taking necessary precautions can make a significant difference in preventing cyber espionage attacks.