With the exponential growth of data in today’s digital age, the need for robust data protection measures has become paramount. The evolution of data protection, from encryption to quantum security, has been a fascinating journey marked by groundbreaking advancements and increasing challenges. As we delve into this topic, let’s explore how data protection has transformed over the years to keep our sensitive information secure.
Data protection has come a long way since the early days of encryption. Encryption, which involves encoding information using complex algorithms, has been the cornerstone of data security for decades. However, with the rise of advanced cyber threats and the advent of quantum computing, traditional encryption methods are becoming vulnerable. This has prompted the exploration of quantum security, a cutting-edge field that leverages the principles of quantum mechanics to develop unbreakable encryption algorithms. The pursuit of quantum security promises enhanced protection against threats and opens up new possibilities for secure data storage and communication.
Introduction: The Importance of Data Protection
Data protection has become an increasingly critical issue in today’s digital age. With the proliferation of online transactions, cloud storage, and interconnected devices, the amount of data being generated and exchanged has skyrocketed. This abundance of data brings with it significant risks, as cybercriminals and hackers seek to exploit vulnerabilities and gain unauthorized access to sensitive information. To counter these threats, various methods of data protection have emerged over the years, evolving from traditional encryption techniques to the emergence of quantum security.
The evolution of data protection has been driven by the need for stronger and more robust security measures that can keep pace with advancing threats. Encryption, which involves encoding information to make it unreadable without the proper decryption key, has long been a cornerstone of data protection. However, as computing power has increased, encryption algorithms have become more vulnerable to cracking. This has necessitated the development of more advanced encryption methods and the exploration of new technologies such as quantum computing for enhanced data security.
In this article, we will explore the evolution of data protection from encryption to quantum security. We will delve into the various techniques and technologies that have been developed, their strengths and weaknesses, and how they contribute to safeguarding sensitive data in today’s digital landscape. Additionally, we will discuss the implications of quantum computing on data protection and the future of secure information exchange.
The Evolution of Encryption
Encryption has long been the bedrock of data protection, serving as a means to ensure the confidentiality and integrity of information. The process involves converting plain, readable text (referred to as plaintext) into an unintelligible form (ciphertext) using an encryption algorithm.
Historically, encryption techniques have been classified into two categories: symmetric encryption and asymmetric encryption.
Symmetric Encryption
Symmetric encryption, also known as secret-key encryption or conventional encryption, relies on a single secret key to both encrypt and decrypt data. This key is shared between the sender and the recipient, and any unauthorized party who gains access to the key can decipher the ciphertext.
One of the most widely used symmetric encryption algorithms is the Advanced Encryption Standard (AES), which was adopted by the U.S. government as a standard for securing sensitive information. AES has been highly regarded for its efficiency and robustness, making it the preferred choice for securing data at rest (stored data) and data in transit (transmitted data).
Despite its strengths, symmetric encryption has limitations. The primary challenge lies in securely distributing the secret key between the sender and the recipient. If the key is compromised during transmission, an attacker can gain access to the encrypted data. Furthermore, because the same key is used for encryption and decryption, the sender and recipient must trust each other with the key’s confidentiality.
Strengths of Symmetric Encryption
- Efficiency: Symmetric encryption algorithms are computationally efficient, making them ideal for high-speed data processing.
- Robustness: Established symmetric encryption algorithms like AES have withstood extensive cryptanalysis and are considered highly secure.
- Used in various applications: Symmetric encryption is widely used in everyday applications, such as secure online communication, virtual private networks (VPNs), and file encryption.
Limitations of Symmetric Encryption
- Key distribution: Sharing the secret key securely between the sender and the recipient can be challenging, especially in large-scale networks or situations where physical exchange of the key is not feasible.
- Key management: As the number of participants in an encrypted communication increases, managing and securely storing all the necessary secret keys becomes increasingly complex.
- Lack of non-repudiation: Symmetric encryption does not provide a way to verify the integrity or origin of a message, as anyone possessing the secret key can generate valid ciphertext.
Asymmetric Encryption
Asymmetric encryption, also known as public-key encryption, employs two mathematically related but distinct keys: a public key and a private key. The public key is widely distributed and available to anyone, while the private key is kept secret by the recipient. Messages encrypted with the recipient’s public key can only be decrypted by their corresponding private key.
Public-key cryptography revolutionized the field of data protection because it eliminated the need for a secure key exchange. Unlike symmetric encryption, where the same key is used for both encryption and decryption, asymmetric encryption provides separate keys for each operation.
The most well-known asymmetric encryption algorithm is the RSA (Rivest-Shamir-Adleman) algorithm, which was developed in the 1970s. RSA has been widely used in securing digital communications, such as SSL/TLS (Secure Sockets Layer/Transport Layer Security) for secure internet browsing.
Strengths of Asymmetric Encryption
- Secure key exchange: Asymmetric encryption eliminates the need for a secure key exchange, as the private key remains known only to the recipient.
- Non-repudiation: The use of digital signatures in asymmetric encryption provides a way to verify the integrity and origin of a message, as the recipient’s private key is required to generate a valid signature.
- Secure communication over insecure channels: Asymmetric encryption enables secure communication even when the communication channel itself is not trusted.
Limitations of Asymmetric Encryption
- Computational overhead: Asymmetric encryption algorithms are computationally more intensive than symmetric encryption algorithms, making them less suitable for resource-constrained devices and high-speed data processing.
- Key length and security: The security of asymmetric encryption is linked to the mathematical complexity of the encryption algorithm and the length of the keys used. Longer key lengths are necessary to withstand potential attacks, which can increase the computational burden.
The Emergence of Quantum Security
With the advancements in computer processing power and the rise of quantum computing, the traditional methods of encryption face new challenges. Quantum computers have the potential to break many of the widely used encryption algorithms, including those considered secure by today’s standards.
Quantum security, also known as post-quantum cryptography, is an emerging field that aims to develop encryption algorithms resistant to attacks by quantum computers. These algorithms utilize mathematical problems that are believed to be computationally hard, even for quantum computers.
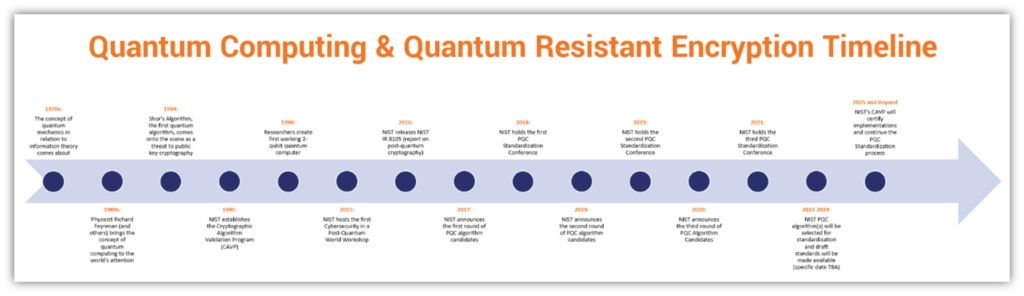
The National Institute of Standards and Technology (NIST) in the United States has been leading the effort to standardize quantum-resistant cryptographic algorithms. The process, known as the NIST Post-Quantum Cryptography Standardization, involves evaluating and selecting new encryption algorithms that can withstand attacks from both classical and quantum computers.
The transition to quantum security presents both challenges and opportunities. On one hand, it necessitates significant research and development efforts to identify and standardize quantum-resistant algorithms. On the other hand, the introduction of quantum computers may also enable new techniques for secure communication and data protection.
Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) is an innovative cryptographic technique that leverages the principles of quantum mechanics to enable secure key exchange between two parties.
QKD uses the properties of quantum particles (such as photons) to communicate data securely. The fundamental principle behind QKD is the impossibility of copying quantum states without disturbing their original properties. This property, known as the “no-cloning theorem,” forms the basis of secure communication in QKD.
QKD offers a high level of security since any attempt to intercept the quantum states or measure them will introduce errors, which can be detected by the communicating parties. If no errors are detected, the shared key is assumed to be secure, as any eavesdropper would have disrupted the quantum states.
While QKD shows promise for secure key exchange, its practical implementation faces challenges such as limited transmission distance due to fiber optic losses and the need for specialized infrastructure. However, research and development in QKD continue to address these limitations and explore its potential applications.
Strengths of Quantum Key Distribution
- Unconditional security: QKD provides unconditional security, as the laws of quantum physics ensure that any attempt to intercept the quantum states will introduce errors.
- Future-proofing: QKD is resistant to attacks by both classical and quantum computers, making it a potential long-term solution for secure key exchange.
Limitations of Quantum Key Distribution
- Infrastructure requirements: QKD requires specialized infrastructure, including the use of single-photon detectors and fiber optic networks, which may limit its widespread adoption.
- Transmission distance: The distance over which secure key exchange can be achieved with QKD is currently limited due to factors such as fiber optic losses.
Conclusion
The evolution of data protection from encryption to quantum security is driven by the ever-increasing need for stronger and more resilient security measures. While encryption methods have served as the foundation of data protection, the rise of quantum computing presents new challenges for traditional encryption algorithms.
Quantum security, with its focus on post-quantum cryptography and techniques like Quantum Key Distribution, holds promise for addressing these challenges. However, practical implementation and widespread adoption of quantum security measures still require further research and development.
As the digital landscape continues to evolve, it is essential to stay informed about the latest advancements in data protection. Adopting robust encryption methods and keeping abreast of the developments in quantum security will be crucial in safeguarding sensitive information in the future.
For further information on the subject, you can visit [https://example.com](https://example.com), a leading resource in data protection and cybersecurity.
The Evolution of Data Protection: From Encryption to Quantum Security
- Encryption has been a widely-used method for protecting data for many years.
- Quantum security is the next generation of data protection, using quantum physics properties to secure information.
- Quantum key distribution (QKD) is a promising technology in quantum security, providing unbreakable encryption keys.
- Quantum-resistant encryption algorithms are being developed to safeguard data against future quantum attacks.
- The evolution of data protection highlights the need for continuous advancements in cybersecurity to keep up with emerging threats.

Over time, the methods used to protect data have evolved to keep up with advancing technology. Initially, encryption was the go-to method for safeguarding sensitive information. Encryption involves converting data into a code that can only be deciphered with a unique key.
However, with the rise of quantum computing, new security measures are needed. Quantum security leverages the bizarre properties of quantum mechanics to create unbreakable codes. This technology is still in its early stages but holds great promise for the future of data protection.