The Evolution of Cybersecurity Posture: Adapting to New Threats is a critical topic in today’s digital landscape. With the rapid advancement of technology and the increasing sophistication of cyber threats, it is essential for organizations to constantly adapt and enhance their cybersecurity measures. In this article, we will explore the changing nature of cybersecurity and the strategies and solutions that have emerged to mitigate the risks.
Cybersecurity has come a long way since its inception. In the early days, it was primarily focused on protecting individual devices and networks from viruses and malware. However, with the rise of the internet and the interconnectedness of systems, the threat landscape has become more complex. According to a recent study, there was a 600% increase in cyber attacks in 2020 alone, highlighting the need for organizations to prioritize their cybersecurity posture. To address these evolving threats, organizations have started to adopt a proactive approach, implementing measures such as multi-factor authentication, encryption, and advanced threat detection systems.

The Constantly Evolving Threat Landscape
The field of cybersecurity has undergone significant changes over the past few decades. As technology advances, so do the tactics used by cybercriminals to infiltrate networks and steal sensitive information. The evolution of cybersecurity posture is a continuous process of adapting to new threats and developing effective defense mechanisms. In this article, we will explore the ever-changing threat landscape and discuss how organizations can adapt their cybersecurity posture to mitigate emerging risks.
The rise of the Internet brought about new opportunities and conveniences, but it also opened the door for cybercriminals to exploit vulnerabilities. Traditional security measures were no longer enough to protect sensitive data and critical infrastructure. As a result, cybersecurity professionals had to continuously evolve their strategies to keep up with the rapidly evolving threat landscape. The evolution of cybersecurity posture involves not only implementing robust security controls but also staying ahead of emerging threats and adopting a proactive approach to defense.
One significant aspect of the evolution of cybersecurity posture is the shift from a reactive to a proactive mindset. In the past, organizations would primarily focus on detecting and responding to cyber threats after they occurred. However, this approach proved to be insufficient against sophisticated attacks that could go undetected for months or even years. Today, organizations understand the importance of proactive threat hunting, vulnerability management, and continuous monitoring to identify and address potential security gaps before they can be exploited.
Cybersecurity best practices play a crucial role in adapting to new threats. It is essential for organizations to stay updated on the latest industry standards, guidelines, and regulations to ensure their cybersecurity posture aligns with the current threat landscape. By implementing a robust cybersecurity framework that includes regular risk assessments, employee awareness training, secure configuration management, and incident response plans, organizations can strengthen their defenses and reduce the likelihood of successful cyber attacks.
The Role of Artificial Intelligence in Cybersecurity
Artificial Intelligence (AI) has emerged as a powerful tool in the fight against cyber threats. With its ability to analyze vast amounts of data and identify patterns, AI can help cybersecurity professionals detect and respond to attacks more effectively. AI-powered threat intelligence platforms can continuously monitor network traffic, analyze system logs, and identify anomalous user behavior, enabling organizations to detect potential breaches in real-time.
AI can also play a significant role in automating routine security tasks, allowing cybersecurity teams to focus on more strategic activities. By leveraging AI for tasks such as threat hunting, vulnerability scanning, and incident response, organizations can improve their overall cybersecurity posture and respond to threats more efficiently. Additionally, AI can help in predicting and preventing attacks by learning from past incidents and proactively identifying potential vulnerabilities in the system.
However, it is important to note that AI is not a foolproof solution and can also be manipulated by threat actors. As AI technology advances, so do the capabilities of cybercriminals to bypass AI-powered security systems. Therefore, it is crucial for organizations to continuously update their AI algorithms and models to stay ahead of emerging threats. Additionally, human oversight and expertise are still necessary to make accurate decisions and assess the potential risks associated with AI-generated insights.
The Importance of User Awareness and Education
One of the most effective ways to improve cybersecurity posture is by ensuring that all users within an organization are aware of the potential risks and are trained to follow best practices. Human error and social engineering attacks remain significant vulnerabilities in cybersecurity defenses. Employees are often the weakest link in the security chain, unintentionally opening the door for cyberattacks through actions like clicking on malicious links or falling victim to phishing emails.
Organizations should prioritize user awareness and education programs to ensure that employees understand the importance of good cyber hygiene and the potential consequences of their actions. Regular training sessions, simulated phishing exercises, and ongoing communication about emerging threats can help create a culture of security within the organization. By empowering employees with the knowledge and skills to identify and report potential threats, organizations can significantly enhance their cybersecurity posture.
Furthermore, implementing strong password policies, enabling multi-factor authentication, and regularly updating software and security patches are essential elements of user awareness and education. Organizations should also establish clear guidelines on the use of personal devices, remote work practices, and data handling procedures to ensure that employees adhere to secure practices both within and outside the office environment.
It is equally important to educate users about emerging threats and the evolving techniques used by cybercriminals. As new attack vectors are discovered, organizations should communicate the risks and provide guidance on how to mitigate them effectively. By fostering a culture of continuous learning and adaptability, organizations can better equip their employees to navigate the ever-changing threat landscape.
The Need for Collaborative Threat Intelligence Sharing
Cybercriminals are constantly sharing information, tools, and techniques in underground forums, allowing them to launch highly coordinated and sophisticated attacks. To effectively defend against these threats, organizations must also collaborate and share threat intelligence within the cybersecurity community. Collaborative threat intelligence sharing enables organizations to gain insights into emerging threats, identify attack trends, and proactively implement countermeasures.
Information sharing can take various forms, such as participating in industry-specific threat intelligence groups, sharing anonymized incident data, and collaborating with trusted partners and vendors. By collectively pooling resources and knowledge, organizations can improve their ability to detect and respond to attacks, ultimately strengthening their cybersecurity posture.
However, information sharing should be done carefully to protect the confidentiality of sensitive data. Organizations should establish clear guidelines and protocols for sharing information, ensuring that personally identifiable information (PII) and other sensitive data are appropriately protected. Compliance with relevant data privacy regulations is essential to maintain trust and confidentiality within the cybersecurity community.
Collaborative threat intelligence sharing not only benefits individual organizations but also contributes to the overall security of the entire ecosystem. By working together, the cybersecurity community can stay one step ahead of cybercriminals and adapt their defenses to the ever-evolving threat landscape.
The Role of Regulation and Compliance
Regulation and compliance play a crucial role in shaping the cybersecurity posture of organizations. Governments and regulatory bodies around the world have recognized the need for robust cybersecurity measures to protect sensitive data and critical infrastructure. Consequently, they have introduced various laws, regulations, and frameworks to enhance cybersecurity practices across industries.
Compliance with industry-specific regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) is essential for organizations that handle sensitive data. These regulations define the necessary security controls and guidelines that organizations must follow to protect personal and confidential information.
Furthermore, regulatory frameworks such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework provide organizations with a set of best practices and standards to develop and improve their cybersecurity posture. Adhering to these frameworks can help organizations establish a strong foundation for their cybersecurity programs and ensure compliance with regulatory requirements.
While regulations and compliance requirements provide a baseline for cybersecurity, it is important for organizations to go beyond minimum requirements. Adopting a risk-based approach and continuously evaluating and enhancing security controls can help organizations stay resilient against emerging threats that may not be explicitly addressed by regulations.
Conclusion
As the threat landscape continues to evolve, organizations must adapt their cybersecurity posture to effectively mitigate new and emerging risks. This evolution involves a proactive approach to threat hunting, the adoption of artificial intelligence tools, user awareness and education programs, collaborative threat intelligence sharing, and compliance with relevant regulations and frameworks. By staying ahead of the curve and implementing robust security measures, organizations can reduce the likelihood of successful cyber attacks and safeguard their data and systems.
Statistics show that the cost of cybercrime continues to rise, emphasizing the importance of continuous improvement in cybersecurity posture. By prioritizing cybersecurity and staying vigilant against new threats, organizations can effectively protect themselves and their stakeholders in an increasingly interconnected digital world.
The Evolution of Cybersecurity Posture: Adapting to New Threats
- As technology advances, so do the threats to our cybersecurity.
- Organizations must continuously adapt their cybersecurity posture to defend against new and evolving threats.
- Cybersecurity is no longer just about firewalls and antivirus software, but also includes employee awareness and training.
- Effective cybersecurity posture involves proactive monitoring and threat intelligence to identify and mitigate potential risks.
- The evolution of cybersecurity posture requires a holistic approach that combines people, processes, and technology.
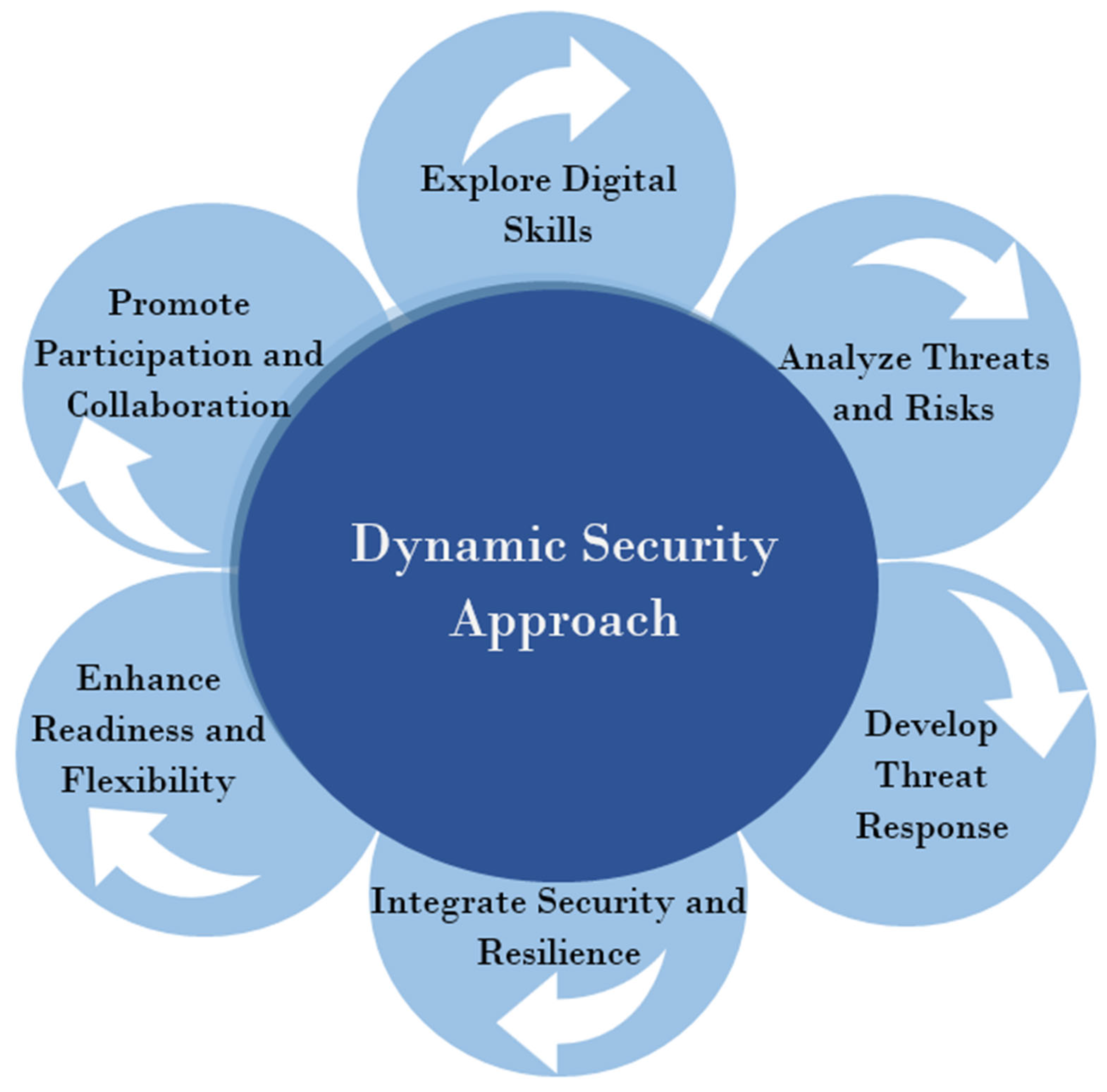
The world of cybersecurity is constantly evolving as new threats emerge.
To protect against these threats, companies and individuals must adapt their cybersecurity posture.
By implementing robust security measures and staying updated on the latest threats, we can defend against cyberattacks.
Cybersecurity is essential for safeguarding personal data, preventing financial loss, and ensuring the smooth operation of businesses.
While the future of cybersecurity may hold unknown challenges, continuous adaptation will be the key to maintaining strong defenses.
Remember, cybersecurity is everyone’s responsibility, and staying informed and proactive is crucial in our digital age.