The Role of Cyber Security in Protecting Against Cyber Espionage is crucial in the digital age we live in. With the increasing sophistication of cyber attacks and the rising threat of state-sponsored hacking, safeguarding sensitive information and preventing unauthorized access has become a top priority for organizations and governments worldwide.
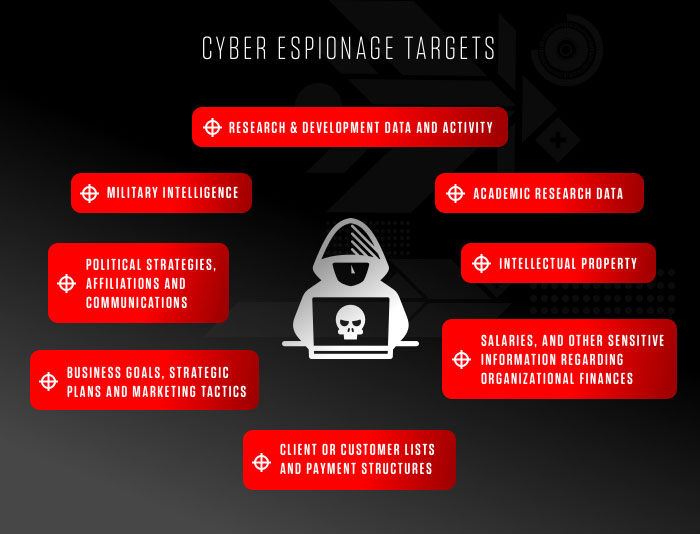
Cyber espionage involves the theft of sensitive data, intellectual property, and national security secrets through digital means. It can have significant consequences, including economic loss, compromised national security, and reputational damage. To combat this threat, cyber security plays a vital role in ensuring the protection of critical infrastructure, detecting and preventing cyber attacks, and safeguarding sensitive information from falling into the wrong hands.

Understanding the Threat of Cyber Espionage
The role of cyber security in protecting against cyber espionage is vital in today’s digital landscape. Cyber espionage refers to the illicit practice of infiltrating computer networks and systems to steal sensitive information, such as classified government data, trade secrets, and intellectual property. It is a clandestine activity carried out by nation-states, criminal organizations, or individuals with the intention of gaining a competitive edge, political advantage, or financial gain.
Cyber espionage poses a significant threat to individuals, businesses, and governments worldwide. The stolen information can be used for various malicious purposes, including blackmail, sabotage, influence campaigns, or selling it to the highest bidder on the dark web. Therefore, safeguarding against cyber espionage requires robust cyber security measures that can detect, prevent, and mitigate potential attacks.
One of the fundamental aspects of protecting against cyber espionage is to understand the tactics, techniques, and procedures employed by threat actors. It involves identifying the vulnerabilities in computer systems and networks that can be exploited, as well as the indicators of compromise that signal a potential breach. By staying informed about the evolving nature of cyber threats, organizations and individuals can better defend themselves against cyber espionage.
The Importance of Cyber Security Measures
Cyber security measures play a crucial role in protecting against cyber espionage. These measures include a combination of technological solutions, best practices, and policies designed to safeguard information systems and data. Here are some key reasons why cyber security is essential in defending against cyber espionage:
- Preventing Unauthorized Access: Cyber security measures help prevent unauthorized individuals or entities from gaining access to sensitive information through various means, such as network breaches, malware, phishing attacks, or social engineering.
- Detecting and Responding to Threats: Cyber security tools and techniques enable the detection and rapid response to potential threats, such as detecting abnormal network activity, identifying malware, or analyzing suspicious behavior.
- Protecting Confidentiality: Confidentiality is a critical aspect of cyber security. Encryption, access controls, and secure data storage are examples of measures that protect sensitive information from falling into the wrong hands.
- Safeguarding Integrity: Cyber security measures ensure the integrity of data and systems, preventing unauthorized modifications, alterations, or tampering that could compromise the accuracy and reliability of information.
- Ensuring Availability: Cyber security policies and technologies ensure the availability of information systems, ensuring that authorized users can access the resources they need when they need them, while keeping malicious actors at bay.
By implementing robust cyber security measures, organizations and individuals can minimize the risk of falling victim to cyber espionage. These measures involve a proactive approach to security, including regular vulnerability assessments, network monitoring, employee training, and incident response planning.
Cyber Threat Intelligence and Information Sharing
Cyber threat intelligence and information sharing play a crucial role in safeguarding against cyber espionage. Cyber threat intelligence involves collecting, analyzing, and disseminating information about potential threats and threat actors. By studying the tactics, techniques, and procedures used by cyber criminals or state-sponsored groups, organizations can better understand their adversaries and stay one step ahead.
Information sharing is another vital aspect of defending against cyber espionage. It involves collaboration and cooperation between different organizations, sectors, and even countries to exchange information about cyber threats, vulnerabilities, and best practices. Sharing information helps to create a collective defense against cyber espionage by pooling resources, expertise, and knowledge to enhance overall cyber security.
Government agencies, industry organizations, and cybersecurity service providers often serve as hubs for cyber threat intelligence and information sharing. They gather and analyze data from various sources, including incident reports, security research, and intelligence agencies, to provide actionable insights to their stakeholders.
Public-Private Partnerships for Combating Cyber Espionage
Public-private partnerships are instrumental in combating cyber espionage. Government agencies and private sector organizations collaborate to share information, resources, and expertise to protect critical infrastructure, national security, and the economy. These partnerships have several benefits:
- Enhanced Information Sharing: Public-private partnerships facilitate the exchange of threat intelligence, incident data, and best practices, enabling both sectors to stay informed about emerging threats and vulnerabilities.
- Coordinated Incident Response: In the event of a cyber attack or a potential breach, public-private partnerships help coordinate and streamline the incident response efforts, allowing for a quick and effective response.
- Strengthened Cyber Resilience: By working together, government and private sector organizations can build cyber-resilient systems and networks, reducing the likelihood of successful cyber espionage attempts.
- Shared Responsibilities: Public-private partnerships recognize that cyber security is a collective responsibility. Through collaboration, both sectors can contribute effectively to securing cyberspace.
Public-private partnerships can take the form of formal agreements, joint task forces, information sharing platforms, or public-private information sharing and analysis centers (ISACs). These collaborations foster trust, promote cross-sector communication, and enable a more coordinated response to the evolving cyber threats posed by cyber espionage.
| Public Sector | Private Sector |
|---|---|
| National security agencies | Technology companies |
| Law enforcement agencies | Financial institutions |
| Cybersecurity agencies | Critical infrastructure operators |
| Defense organizations | Retail and e-commerce businesses |
The Role of Cyber Security Professionals
Cyber security professionals are at the forefront of protecting against cyber espionage. Their role is multifaceted and involves various responsibilities:
- Developing and Implementing Security Measures: Cyber security professionals are responsible for designing, implementing, and maintaining security controls, such as firewalls, intrusion detection systems, and encryption protocols, to protect against cyber espionage.
- Monitoring and Analyzing Network Activity: They continuously monitor network activity, looking for signs of suspicious or anomalous behavior that may indicate a potential cyber espionage attempt.
- Conducting Vulnerability Assessments: Cyber security professionals perform regular vulnerability assessments to identify weaknesses in computer systems and networks that could be exploited by threat actors.
- Incident Response and Forensics: In the event of a cyber attack or a data breach, cyber security professionals play a critical role in investigating the incident, mitigating the damage, and helping organizations recover.
- Educating and Training Employees: They conduct cybersecurity awareness programs and provide training to employees, equipping them with the knowledge and skills necessary to recognize and respond to cyber threats.
Cyber security professionals also stay up to date with the latest threats, trends, and technologies in the field of cyber security by attending conferences, obtaining certifications, and participating in professional organizations. Their expertise and dedication are essential in the ongoing battle against cyber espionage.
Conclusion
The role of cyber security in protecting against cyber espionage cannot be overstated. It is crucial for individuals, businesses, and governments to implement robust cyber security measures, stay informed about emerging threats, and collaborate through public-private partnerships. By taking a proactive approach to cyber security, organizations and individuals can mitigate the risks associated with cyber espionage and safeguard their sensitive information.
Remember, cyber security is an ongoing process that requires continuous monitoring, assessment, and improvement. It is essential to remain vigilant and adapt to the ever-evolving threat landscape to stay one step ahead of cybercriminals engaged in cyber espionage.
This article was brought to you by **[Cybersecure Solutions](https://www.cybersecuresolutions.com)**, a leading cyber security provider offering comprehensive solutions to protect against cyber espionage and other cyber threats. With their expertise and cutting-edge technologies, Cybersecure Solutions empowers organizations to secure their digital assets and maintain a strong defense against cyber espionage.The Role of Cyber Security in Protecting Against Cyber Espionage
- Strong cyber security measures are essential in safeguarding against cyber espionage.
- Implementing robust firewalls and encryption technologies can help prevent unauthorized access to sensitive information.
- Regularly updating security software and conducting vulnerability assessments can help identify and mitigate potential weaknesses in a system.
- Employee training and awareness programs play a critical role in preventing social engineering attacks and promoting a security-first mindset.
- Cyber threat intelligence and monitoring tools can detect and respond to suspicious activities, enabling quick action to mitigate potential damage.
Cyber security plays a crucial role in protecting against cyber espionage.
It safeguards sensitive information, detects and prevents cyber attacks, and ensures a safe digital environment.
With cyber security measures in place, individuals and organizations can defend against intrusions and unauthorized access.
By staying vigilant and implementing strong passwords, firewalls, and encryption, we can stay protected from cyber threats.
Remember, cyber security is everyone’s responsibility in the digital world we live in!