As technology continues to advance at an exponential rate, so does the ever-present threat of cyber attacks. Cybersecurity has become a vital aspect of our digital world, protecting individuals and organizations from various forms of malicious activities. One critical aspect of securing our systems is through the implementation of endpoint detection and response (EDR) solutions.
Endpoint detection and response (EDR) plays a crucial role in safeguarding computer systems and networks against cyber threats. By monitoring and analyzing endpoint activities, EDR solutions are able to detect and respond to potential threats in real-time. With the ability to identify suspicious behavior and flag potential security breaches, EDR acts as a frontline defense mechanism, bolstering the overall cybersecurity posture of organizations.
Introduction: Understanding Endpoint Detection and Response in Cybersecurity
In today’s digital landscape, the need for robust cybersecurity measures has never been more critical. As cyber threats continue to evolve and become more sophisticated, organizations must stay one step ahead to protect their sensitive data and systems. One effective approach to combatting these threats is through the implementation of Endpoint Detection and Response (EDR) solutions.
Endpoint Detection and Response refers to the process of proactively identifying, investigating, and mitigating security incidents on network endpoints such as computers, laptops, mobile devices, and servers. These endpoints serve as the entry points for cyberattacks and are often targeted by malicious actors seeking to gain unauthorized access or exploit vulnerabilities.
In this article, we will explore the role of Endpoint Detection and Response in cybersecurity, its key features and benefits, and how it can help organizations enhance their overall security posture. We will delve into the various facets of EDR, including its components, deployment strategies, and the importance of integrating EDR into a comprehensive security framework.
The Benefits and Importance of Endpoint Detection and Response
Endpoint Detection and Response solutions offer several significant benefits that contribute to a strong cybersecurity posture. By understanding these advantages, organizations can comprehend the importance of EDR and make informed decisions when selecting and implementing these solutions.
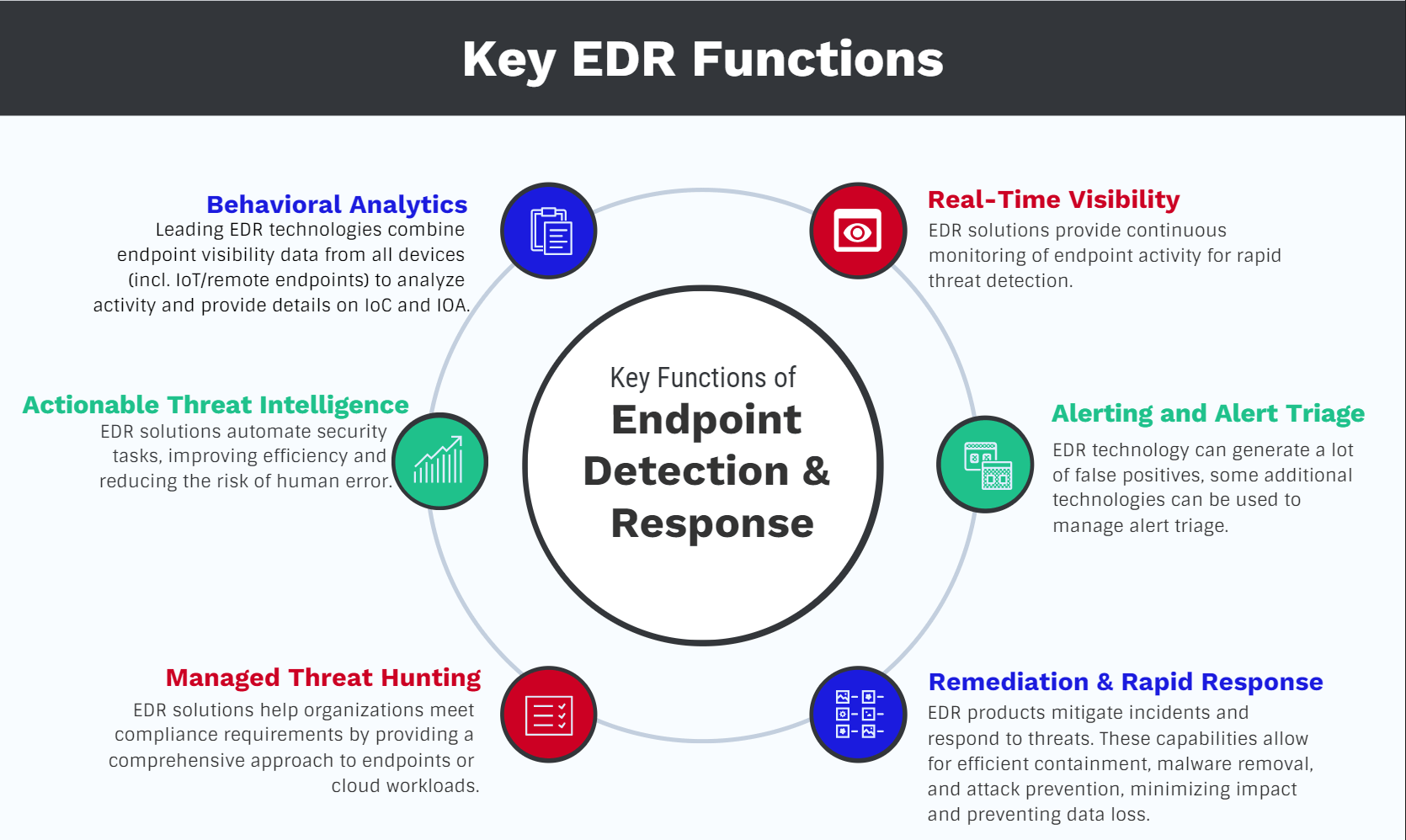
1. Early Detection of Threats: Endpoint Detection and Response solutions continuously monitor endpoints for any suspicious activities or anomalies. By analyzing real-time data, EDR tools can detect potential threats at their earliest stages, allowing organizations to respond promptly and prevent further damage.
2. Rapid Incident Response: When a security incident occurs, time is of the essence. EDR solutions provide organizations with the necessary tools and capabilities to investigate and respond to incidents quickly. By streamlining the incident response process, EDR helps minimize the impact of breaches and reduces downtime.
3. Proactive Threat Hunting: In addition to monitoring for known threats, Endpoint Detection and Response solutions enable proactive threat hunting. This involves actively searching for signs of suspicious activities or potential threats, even if they have not yet triggered any alarms or alerts.
4. Enhanced Visibility and Control: EDR solutions provide organizations with comprehensive visibility into their endpoints, including detailed information about activities, processes, and network traffic. This visibility allows security teams to gain a holistic understanding of the organization’s security posture and gives them greater control over their environment.
By leveraging the benefits of Endpoint Detection and Response, organizations can significantly improve their cybersecurity defenses and reduce the risk of successful cyberattacks. These solutions are especially valuable for enterprises that handle sensitive data or operate in industries with stringent compliance and regulatory requirements.
Endpoint Detection and Response Components
Endpoint Detection and Response solutions consist of several key components that work together to provide comprehensive protection against cyber threats. Let’s explore these components in detail:
1. Endpoint Agents
Endpoint agents are software programs installed on individual endpoints to monitor activities, collect data, and send information to the central EDR system. These agents act as the eyes and ears of the EDR solution, continuously gathering real-time data about processes, network connections, and system events.
The information collected by endpoint agents is crucial for detecting and responding to security incidents. These agents can also quarantine or mitigate threats autonomously based on predefined rules and policies.
Endpoint agents should be lightweight, unobtrusive, and capable of operating in both online and offline environments. They should also have the ability to update their detection capabilities and be immune to tampering or removal by malicious actors.
2. Centralized Management Console
The centralized management console serves as the command center for the EDR solution. It provides security teams with a single interface to monitor, manage, and analyze endpoint data and security events. This console enables administrators to configure policies, create rules, and define automated responses.
The centralized management console should have robust reporting and analysis capabilities, allowing security teams to gain insights into the organization’s security posture, identify trends, and respond effectively to emerging threats. It should also facilitate collaboration among security professionals and streamline incident response processes.
Moreover, the management console should integrate with other security tools and systems, such as Security Information and Event Management (SIEM) platforms, to provide a unified view of the organization’s security landscape.
3. Threat Intelligence Integration
Endpoint Detection and Response solutions leverage external threat intelligence sources to enhance their detection and response capabilities. These threat intelligence feeds provide real-time information about the latest malware, vulnerabilities, and hacker tactics.
Integrating threat intelligence with an EDR solution enables organizations to stay up to date with the evolving threat landscape and adapt their security controls accordingly. By leveraging this intelligence, EDR solutions can identify and respond to emerging threats more effectively.
Threat intelligence integration should be automated and seamless, ensuring that the EDR solution keeps pace with the rapidly evolving threat landscape without placing an additional burden on security teams.
Endpoint Detection and Response Deployment Strategies
Organizations have several deployment options when implementing Endpoint Detection and Response solutions, depending on their specific requirements and resources. Let’s explore some common deployment strategies:
1. On-Premises Deployment
With on-premises deployment, the EDR solution is hosted and managed within the organization’s own infrastructure. This approach allows organizations to maintain full control over their data and security processes, making it an attractive choice for highly regulated industries or those with strict data sovereignty requirements.
On-premises deployment requires organizations to allocate resources for infrastructure, maintenance, and updates. It also necessitates skilled IT personnel to manage and monitor the system effectively.
2. Cloud-Based Deployment
Cloud-based deployment involves hosting the EDR solution on cloud platforms provided by third-party vendors. This deployment strategy offers scalability, flexibility, and reduced maintenance costs since the vendor takes care of infrastructure management and updates.
Cloud-based deployment is particularly beneficial for organizations with distributed workforces, as it allows easy deployment and management of the EDR solution across multiple locations. It also provides seamless integration with other cloud-based security services and allows for quicker deployment and updates.
3. Managed EDR Services
Managed EDR services are offered by external managed security service providers (MSSPs). With this deployment approach, organizations outsource the management, monitoring, and response tasks to third-party experts who specialize in EDR.
Managed EDR services enable organizations to leverage the expertise and experience of MSSPs, who can provide round-the-clock monitoring, incident response, and threat hunting capabilities. This option is particularly suitable for organizations with limited in-house resources or those looking to augment their existing security team’s capabilities.
When choosing a deployment strategy, organizations should consider factors such as their budget, in-house expertise, scalability requirements, and compliance obligations.
Integrating Endpoint Detection and Response into a Comprehensive Security Framework
Endpoint Detection and Response solutions are most effective when integrated into a broader security framework that encompasses various security technologies, best practices, and policies. Let’s explore the key considerations for integrating EDR into a comprehensive security framework:
1. Endpoint Protection Platforms (EPP)
Endpoint Protection Platforms (EPP) offer foundational security capabilities such as antivirus, anti-malware, and firewall protection. Integrating EDR with EPP solutions provides organizations with a holistic defense against both known and unknown threats.
By combining the prevention capabilities of EPP with the detection and response capabilities of EDR, organizations can enhance their overall security posture and ensure comprehensive protection for their endpoints.
2. Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) platforms collect, analyze, and correlate security events and logs across the organization’s network. Integrating EDR with a SIEM solution allows for centralized visibility and correlation of endpoint events with other security events, providing a unified view of the organization’s security landscape.
By sharing data and insights between EDR and SIEM, organizations can improve their threat detection capabilities, identify patterns of attack, and respond quicker to security incidents.
3. User Behavior Analytics (UBA)
User Behavior Analytics (UBA) platforms monitor and analyze user behavior patterns to identify anomalies or suspicious activities that may indicate insider threats or compromised accounts. Integrating UBA with EDR enables organizations to gain a deeper understanding of user activities on endpoints and identify potential security risks.
By analyzing both user behavior and endpoint data, organizations can enhance their ability to detect and respond to sophisticated threats, such as advanced persistent threats (APTs) and insider attacks.
4. Incident Response Planning
Endpoint Detection and Response should be an integral part of an organization’s incident response planning. By defining clear roles and responsibilities, establishing communication channels, and conducting regular incident response exercises, organizations can ensure a coordinated and effective response to security incidents.
When developing an incident response plan, organizations should consider the specific capabilities and features offered by their EDR solution and align them with their incident response objectives.
Conclusion
Endpoint Detection and Response plays a crucial role in modern cybersecurity by proactively identifying and responding to security incidents on endpoints. These solutions offer numerous benefits, including early threat detection, rapid incident response, proactive threat hunting, and enhanced visibility and control.
By integrating EDR into a comprehensive security framework and leveraging other security technologies, organizations can further enhance their cybersecurity defenses and reduce the risk of successful cyberattacks.
Key Takeaways
- Endpoint Detection and Response (EDR) plays a crucial role in protecting against cyber threats.
- EDR solutions provide real-time monitoring and analysis of endpoints to detect and respond to security incidents.
- By leveraging advanced technologies like artificial intelligence and machine learning, EDR can identify and prevent unknown threats.
- EDR provides visibility into endpoint activities, helping organizations identify vulnerabilities and strengthen their security posture.
- With the increasing sophistication of cyber attacks, implementing EDR is essential to minimize the risk of data breaches and protect sensitive information.

Cyber security is important. One way to protect against threats is with Endpoint Detection and Response (EDR). This technology can detect and respond to malicious activities on devices like computers and smartphones. It can help prevent data breaches and keep personal information safe.
EDR works by monitoring and analyzing device activities in real-time. It can identify suspicious behavior and isolate potential threats. By having EDR in place, users can have peace of mind knowing that their devices are protected from cyber attacks.