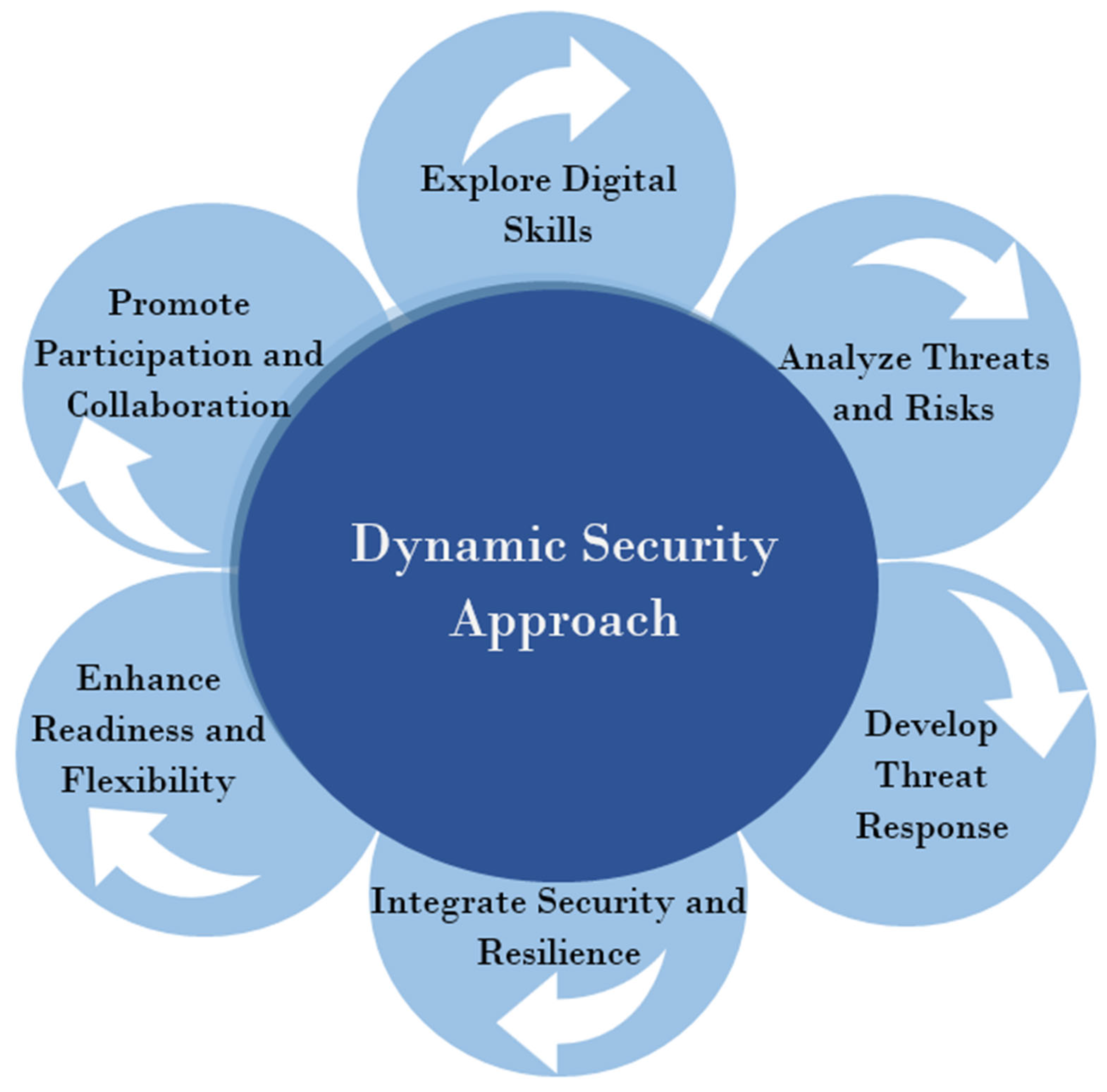
With the rapid growth of technology and the increasing threats to our environment, exploring the potential of cyber security in environmental monitoring and conservation has become more crucial than ever. As we continue to rely on interconnected systems and data-driven solutions, protecting our natural resources from cyber attacks and misuse becomes an essential part of ensuring their preservation for future generations.
Cyber security in environmental monitoring and conservation involves utilizing advanced technologies and protocols to safeguard the data collected from various environmental sensors, satellite imagery, and other monitoring systems. By implementing robust cyber security measures, we can prevent unauthorized access, data breaches, and manipulation of crucial environmental data. This not only helps in maintaining the integrity and accuracy of the information but also enables effective decision-making and policy implementation for the protection and sustainable management of our ecosystems.

The Role of Cyber Security in Environmental Monitoring and Conservation
In today’s digital age, cyber security plays a crucial role in various aspects of our lives, including environmental monitoring and conservation efforts. With the increasing reliance on technology and connectivity, there is a need to ensure the security and integrity of the systems used in monitoring and protecting our environment. Cyber attacks and data breaches can have severe consequences, not only for organizations and individuals but also for the environment itself. Therefore, exploring the potential of cyber security in environmental monitoring and conservation is of utmost importance.
One aspect of cyber security in environmental monitoring is the protection of data collected from various sources such as remote sensors, satellites, and drones. These data sources provide valuable insights into the state of the environment, including air quality, water quality, temperature, and biodiversity. Ensuring the confidentiality, integrity, and availability of this data is crucial for accurate analysis and decision-making. Cyber security measures such as encryption, access control, and secure data storage can help protect the integrity and privacy of the collected data.
Additionally, cyber security can also play a role in the prevention and detection of environmental crimes, such as illegal wildlife trade and deforestation. The use of advanced technologies and monitoring systems can help identify suspicious activities and alert authorities to take appropriate action. By leveraging cyber security measures, such as surveillance cameras, facial recognition, and machine learning algorithms, it becomes possible to establish a robust monitoring infrastructure that can deter and detect environmental crimes effectively.
As the world becomes more interconnected and reliant on technology, cyber security will continue to play a pivotal role in safeguarding our environment. By investing in robust cyber security measures, we can ensure the integrity of environmental monitoring systems, protect sensitive data, and combat environmental crimes. It is essential for researchers, policymakers, and organizations involved in environmental monitoring and conservation to understand the potential of cyber security and implement necessary measures to secure the future of our planet.
Enhancing Data Security in Environmental Monitoring
Data security is a critical concern in environmental monitoring, as the accuracy and reliability of the data collected directly impact decision-making and conservation efforts. Cyber security measures can help ensure the secure transmission, storage, and analysis of environmental data, minimizing the risk of data breach and manipulation.
1. Secure Data Transmission
One of the key challenges in environmental monitoring is the secure transmission of data from remote sensors and monitoring devices to centralized systems. These sensors and devices are often located in remote areas, making them vulnerable to cyber attacks. Encryption techniques can be applied to protect the data during transmission, ensuring its confidentiality and integrity. By using encryption algorithms, data can be securely transmitted over networks, minimizing the risk of unauthorized access or tampering.
In addition to encryption, secure communication protocols such as Transport Layer Security (TLS) can be implemented to establish a secure connection between the sensors/devices and the central monitoring system. TLS ensures the authenticity and integrity of the data by verifying the identity of the communicating parties and encrypting the data exchanged between them. By implementing secure data transmission protocols, the risk of data interception or manipulation during transit can be significantly reduced.
Furthermore, organizations involved in environmental monitoring can also implement measures such as virtual private networks (VPNs) to create secure connections between remote sensors and central systems. VPNs provide a secure tunnel for data transmission, encrypting the data and ensuring its secure passage through potentially insecure networks. This helps to protect the data from interception and unauthorized access.
2. Robust Data Storage
Once the data is collected and transmitted securely, it needs to be stored in a secure manner to prevent unauthorized access or data loss. Cyber security measures such as access controls, encryption, and regular backups can help protect the integrity and availability of the stored data.
Access controls ensure that only authorized individuals have the necessary permissions to access the data. This can be achieved through user authentication mechanisms such as usernames, passwords, and multi-factor authentication. By implementing strong access controls, organizations can prevent unauthorized access to the data and mitigate the risk of data breaches.
In addition to access controls, encrypting the stored data adds an extra layer of security. Encryption converts the data into an unreadable format, and only authorized individuals with the decryption key can access the data. In the event of a data breach or physical theft of storage devices, encrypted data remains protected and inaccessible to unauthorized individuals.
Regular backups of the stored data are essential to prevent data loss in case of accidental deletion, hardware failure, or cyber attacks. Backups should be stored in secure off-site locations or cloud platforms with proper access controls and encryption to ensure the availability and durability of the data. By implementing a robust data storage strategy, organizations can safeguard the integrity and availability of environmental data.
3. Threat Monitoring and Incident Response
In addition to preventive measures, organizations involved in environmental monitoring should also have robust threat monitoring and incident response mechanisms in place. Continuous monitoring of network activities, system logs, and user behavior can help identify suspicious activities and potential cyber threats.
By implementing intrusion detection and prevention systems, organizations can proactively detect and prevent cyber attacks. These systems monitor network traffic, looking for patterns and signatures associated with known cyber threats. In the event of a detected threat, the systems can automatically take preventive actions such as blocking the suspicious traffic or alerting the IT security team.
Furthermore, organizations should establish robust incident response plans to address cyber security incidents effectively. These plans should outline the steps to be taken in the event of a breach or incident, including notifying the appropriate authorities, conducting forensic investigations to determine the cause and extent of the breach, and implementing remedial measures to prevent future incidents. By having a well-defined incident response plan, organizations can minimize the impact of cyber security incidents on their environmental monitoring operations.
Combating Environmental Crimes through Cyber Security
In addition to enhancing data security in environmental monitoring, cyber security measures can also play a crucial role in combating environmental crimes. The illegal wildlife trade, deforestation, and other forms of environmental degradation are major global issues that require effective monitoring and enforcement.
1. Surveillance and Monitoring Systems
Advanced surveillance and monitoring systems can leverage cyber security technologies to detect and deter environmental crimes. These systems can be equipped with surveillance cameras, satellite imagery, and drones to monitor protected areas and identify potential threats.
Cyber security measures such as facial recognition algorithms, machine learning, and pattern recognition can be applied to analyze the collected data and identify suspicious activities. For example, facial recognition technology can help identify individuals involved in the illegal wildlife trade, allowing authorities to take appropriate action.
Moreover, integrated monitoring systems can generate real-time alerts and notifications when potential environmental crimes are detected. These alerts can be sent to law enforcement agencies, park rangers, and other relevant authorities, enabling prompt action to prevent further damage.
2. Digital Forensics and Investigation
Cyber security technologies and practices, such as digital forensics, can play a vital role in investigating environmental crimes. Digital forensics involves the collection, preservation, analysis, and presentation of digital evidence in a manner that maintains its integrity and admissibility in court.
When it comes to environmental crimes, digital evidence can include data from surveillance cameras, social media posts, online communications, and financial transactions. By applying digital forensic techniques, investigators can gather and analyze the digital evidence, linking individuals to the crimes and providing solid evidence for prosecution.
These techniques can also be used to trace the origins of illegally traded wildlife products or the sources of illegal logging activities. By analyzing the digital footprints left by criminals, law enforcement agencies can identify the key players in environmental crimes and dismantle criminal networks.
3. International Collaboration and Information Sharing
Cyber security can facilitate international collaboration and information sharing to combat environmental crimes more effectively. By establishing secure communication channels and information-sharing platforms, law enforcement agencies, environmental organizations, and other stakeholders can collaborate and exchange information in real-time.
Through these platforms, valuable insights and intelligence can be shared, allowing authorities to track the movement of illegal wildlife, identify smuggling routes, and coordinate enforcement efforts. By leveraging cyber security measures such as encrypted communication and access controls, the security and integrity of the shared information can be maintained.
In conclusion, exploring the potential of cyber security in environmental monitoring and conservation is crucial for ensuring the integrity of data, protecting the environment, and combating environmental crimes. By implementing robust cyber security measures, organizations can enhance the security and integrity of environmental data, safeguard against cyber threats, and facilitate international collaboration and information sharing. It is imperative for researchers, policymakers, and organizations involved in environmental monitoring and conservation to continue exploring the potential of cyber security and implementing necessary measures to secure our planet’s future.
For more information on how cyber security is shaping environmental monitoring and conservation efforts, click here.
Key Takeaways
- Cyber security plays a crucial role in environmental monitoring and conservation.
- Using cyber security measures ensures the confidentiality, integrity, and availability of environmental data.
- It helps protect against cyber threats that could compromise environmental monitoring systems.
- Cyber security also safeguards sensitive information related to conservation efforts.
- Implementing robust cyber security measures is essential for maintaining the reliability and accuracy of environmental monitoring systems.

Cyber security is crucial in protecting environmental monitoring and conservation efforts.
By safeguarding data and preventing hacking, cyber security ensures the integrity of vital information.
This helps in the accurate tracking of environmental changes and the protection of wildlife habitats.
Through advanced technologies, cyber security can enhance the efficiency of monitoring systems, enabling real-time alerts.
By strengthening network defenses, cyber security minimizes the risk of cyber attacks that could disrupt environmental monitoring operations.
As technology continues to advance, the need for robust cyber security measures in environmental monitoring and conservation will only grow.
By adopting these measures, we can protect our planet’s precious ecosystems for future generations to enjoy.