Securing IoT ecosystems is crucial to protect sensitive data and prevent unauthorized access. Implementing strong authentication methods, such as multi-factor authentication, helps ensure only authorized users can access IoT devices and networks. Regular software updates and patching also play a crucial role in addressing security vulnerabilities. Employing robust encryption mechanisms and using secure protocols, like HTTPS, further enhance the security of IoT ecosystems. Additionally, implementing intrusion detection and prevention systems helps detect and mitigate potential threats. Overall, a comprehensive security strategy is essential to safeguard IoT ecosystems.
Securing IoT ecosystems has become an increasingly crucial task in our interconnected world. With the proliferation of smart devices and the exponential growth of data being generated and transmitted, the need to protect these ecosystems from cyber threats has never been more critical. Every day, countless devices connect to the internet, from smart thermostats and home security systems to industrial sensors and medical devices. Ensuring the security of these devices and the data they generate is of paramount importance to safeguard privacy, prevent unauthorized access, and mitigate potential risks.
The security challenges posed by IoT ecosystems are multifaceted. One significant aspect is the sheer scale and diversity of the devices and technologies involved. From legacy systems to cutting-edge IoT devices, each with its own vulnerabilities and potential attack vectors, securing the entire ecosystem requires comprehensive strategies and solutions. Moreover, the rapid pace of technological innovation often outpaces security measures, leaving vulnerabilities that can be exploited by cybercriminals. As a result, there is a critical need for proactive security measures, including robust authentication protocols, secure data encryption, frequent software updates, and effective threat detection systems. By implementing these measures, organizations and individuals can better protect their IoT systems and ensure the integrity and confidentiality of their data.
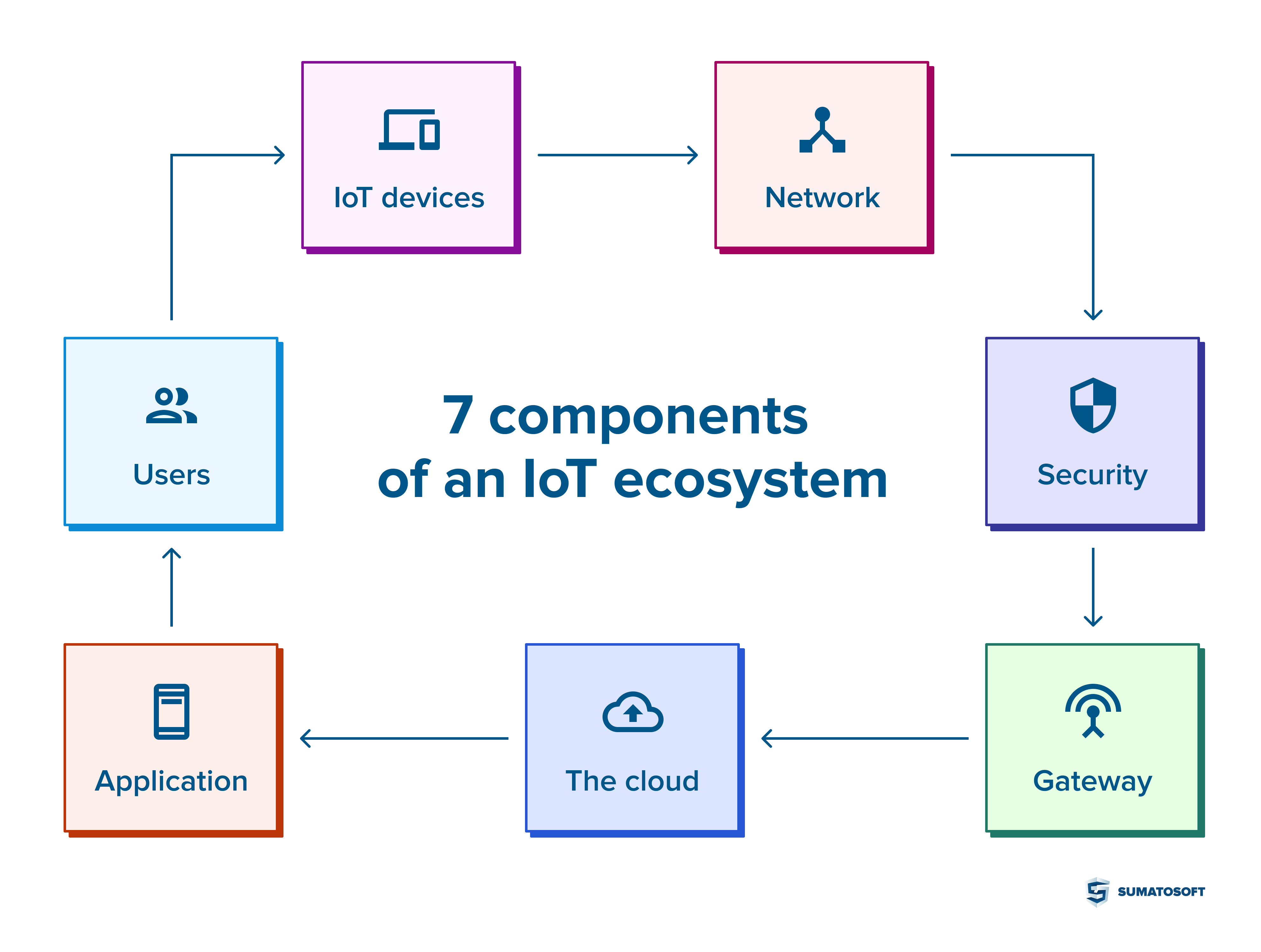 Source: sumatosoft.com
Source: sumatosoft.com
The Importance of Securing IoT Ecosystems
Securing internet of things (IoT) ecosystems is of critical importance in today’s connected world. With the rapid growth of IoT devices, which include everything from smart home appliances to industrial systems, ensuring the security and privacy of these ecosystems has become a top priority. IoT devices are uniquely vulnerable to cyberattacks due to their wide range of interconnectedness and often weak security measures. In fact, a survey conducted by Cybersecurity Ventures predicted that cybercrime will cost the world $10.5 trillion annually by 2025, with IoT attacks being a significant contributing factor. To protect these systems and safeguard sensitive data, it is essential to implement robust cybersecurity measures.
One of the key challenges in securing IoT ecosystems is the sheer scale and complexity of these networks. IoT devices are typically interconnected through different communication protocols, making them susceptible to attacks at various points. Moreover, unlike traditional computing devices, IoT devices often lack the computing power and storage capacity to implement sophisticated security measures. This makes them attractive targets for cybercriminals who can exploit vulnerabilities to gain unauthorized access, causing disruptions, compromising data, and even posing physical risks. To address these challenges and mitigate potential risks, organizations need to adopt a holistic approach to IoT security.
One way to secure IoT ecosystems is to ensure that all devices and components within the network are equipped with up-to-date and robust security measures. This includes implementing strong encryption algorithms, enforcing secure authentication mechanisms, and regularly patching and updating software. It is also crucial to establish secure communication channels and implement access controls to prevent unauthorized access to sensitive information. Additionally, organizations should consider adopting a zero-trust security model, where each device and user is verified and authenticated before granting access to the network. This approach helps minimize the potential damage caused by compromised devices or malicious actors.
To learn more about the importance of securing IoT ecosystems and the latest practices in IoT cybersecurity, you can visit [this insightful article](https://thoughts.tech/2023/12/15/cybersecurity-for-iot-securing-the-connected-world/) that provides valuable insights and recommendations for protecting the connected world.
Securing IoT Ecosystems: Best Practices
In this section, we will explore some of the best practices for securing IoT ecosystems and protecting against potential cyber threats. By following these guidelines, organizations can increase the resilience of their IoT networks and minimize the risks associated with unauthorized access and data breaches.
1. Conduct a Comprehensive Risk Assessment
Before implementing any security measures, it is crucial to conduct a thorough risk assessment to identify potential vulnerabilities and prioritize security efforts. This includes assessing the potential impact of a security breach on different IoT devices and identifying the most critical assets within the ecosystem. By understanding the risks and vulnerabilities specific to their IoT network, organizations can develop targeted security strategies and allocate resources effectively.
Furthermore, organizations should consider the impact of an IoT security breach on business operations, customer trust, and regulatory compliance. By evaluating the potential consequences, organizations can justify investments in cybersecurity and secure the necessary resources to safeguard IoT ecosystems effectively.
To conduct a comprehensive risk assessment, it is essential to involve relevant stakeholders, including IT departments, cybersecurity experts, and business leaders. Their collective expertise can help identify potential threats, assess the adequacy of existing security controls, and develop a tailored security framework for securing IoT ecosystems.
In addition to conducting a risk assessment internally, organizations can also seek external audits and security assessments from independent third parties. These audits provide an unbiased evaluation of the organization’s cybersecurity posture and help identify potential blind spots and areas for improvement.
2. Implement Strong Authentication and Access Controls
One of the fundamental aspects of securing IoT ecosystems is implementing robust authentication and access controls. This involves ensuring that only authorized devices and users can access the network and perform specific actions. Here are some best practices for strong authentication and access controls in IoT environments:
- Use strong, unique passwords or passphrases for each IoT device and associated user account.
- Enable two-factor authentication (2FA) or multi-factor authentication (MFA) to add an extra layer of security.
- Implement role-based access controls (RBAC) to define and restrict the privileges of different users and devices.
- Regularly review and update access controls to reflect changes in device ownership or user roles.
By implementing strong authentication and access controls, organizations can prevent unauthorized devices or individuals from accessing critical systems and data. It is crucial to balance usability and security to ensure that security measures do not hinder the functionality and convenience of IoT devices.
3. Encrypt Data in Transit and at Rest
To protect sensitive information transmitted between IoT devices and networks, it is essential to encrypt data in transit. This prevents unauthorized entities from intercepting and accessing the data. Likewise, it is equally important to encrypt data at rest, ensuring that if a device is compromised, the data stored on it remains inaccessible.
Encryption algorithms, such as Advanced Encryption Standard (AES), can be used to protect data confidentiality. It is crucial to choose encryption algorithms and key sizes that are strong enough to withstand potential attacks. Regularly updating encryption protocols and algorithms is also necessary to counter emerging threats and vulnerabilities.
Organizations should also consider implementing secure communication protocols, such as Transport Layer Security (TLS), for data transmission. TLS ensures the integrity and confidentiality of data exchanged between devices, protecting against eavesdropping and tampering.
4. Regularly Update and Patch IoT Devices
IoT devices often rely on embedded software and firmware, which can contain vulnerabilities that are discovered over time. To mitigate the risk of exploitation, organizations must regularly update and patch their IoT devices. This includes applying security updates released by device manufacturers and ensuring that devices are running the latest version of their firmware.
To streamline the maintenance and update process, organizations can adopt device management platforms that enable centralized monitoring and control of IoT devices. These platforms help organizations identify devices that require updates, manage version control, and track the overall security posture of the IoT ecosystem.
In addition to updating the firmware, organizations should also consider disabling or removing any unnecessary services or features that may introduce security risks. By minimizing the attack surface, organizations can reduce the potential vulnerabilities that can be exploited by malicious actors.
Furthermore, organizations should establish robust device decommissioning procedures to ensure that IoT devices are properly retired at the end of their lifecycle. This includes securely erasing sensitive data, disconnecting devices from the network, and disposing of devices following industry best practices.
5. Monitor and Detect Anomalies
Continuous monitoring and anomaly detection are essential components of a proactive IoT security approach. By monitoring network traffic, device behavior, and data exchanges, organizations can identify potential security incidents or unusual activities that may indicate a compromise.
Implementing an Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) can aid in detecting and responding to potential threats in real-time. These systems analyze network traffic and device logs, comparing them against known threat signatures or behavioral patterns to identify anomalies. If a potential threat is detected, the system can trigger an alert or implement proactive measures to prevent further damage.
Organizations should also establish incident response plans and procedures to handle potential security incidents effectively. This includes defining roles and responsibilities, establishing communication channels, and conducting regular drills and simulations to test the response capabilities of the organization.
By proactively monitoring and detecting anomalous activities, organizations can identify potential security breaches before they cause significant damage and take appropriate action to minimize the impact on the IoT ecosystem.
For more detailed information and additional best practices on securing IoT ecosystems, you can visit [this comprehensive article](https://thoughts.tech/2023/12/15/cybersecurity-for-iot-securing-the-connected-world/).
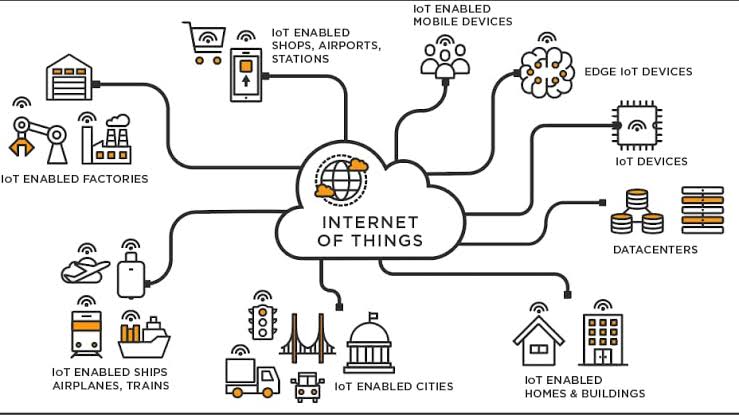
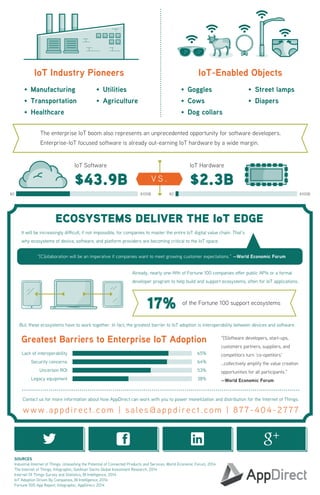
Securing IoT ecosystems is crucial to protect our devices and data.
By following best practices like using strong passwords and regularly updating firmware, we can minimize vulnerabilities.
Additionally, being cautious when connecting to public networks and disabling unnecessary features can further enhance security.
Ultimately, staying informed about potential risks and being proactive in implementing security measures will help safeguard our IoT ecosystems.